Enterprises of all size and shape have to manage their employees, customers, and partners access to a variety of information. In most cases passwords are used as a gate-keeper to prevent unauthorized access to data and digital services. Passwords do an insufficient job at protecting said information and they also make it difficult for us to access the services we need for work, health, and entertainment purposes. In this article we’re trying to be as agnostic as possible whether you think about deploying passkeys to your workforce or customers. Some parts might be more relevant for one or the other of these scenarios.
When moving away from passwords, there is not one unique replacement, but rather a multitude of options that provide different grades of security, privacy, and may not be available to everyone in every situation. One of the most promising new standards is passkeys, built on FIDO2 and WebAuthn, that allows passwordless authentication on most modern platforms.
This article aims at giving Identity- or Security- professionals talking points and a framework to champion the adoption of passkeys within their organization. This consists of three main elements.
If you’re interested in reading up on what passkeys are and how they can help to reduce our reliance on passwords visit the website of the FIDO Alliance.
Why should an organization adopt passkeys?
Before you go out there and champion the move to passkeys in your organization, we should agree on some basics on what problems in your organization can be solved by reducing the reliance on passwords and introducing passkeys.
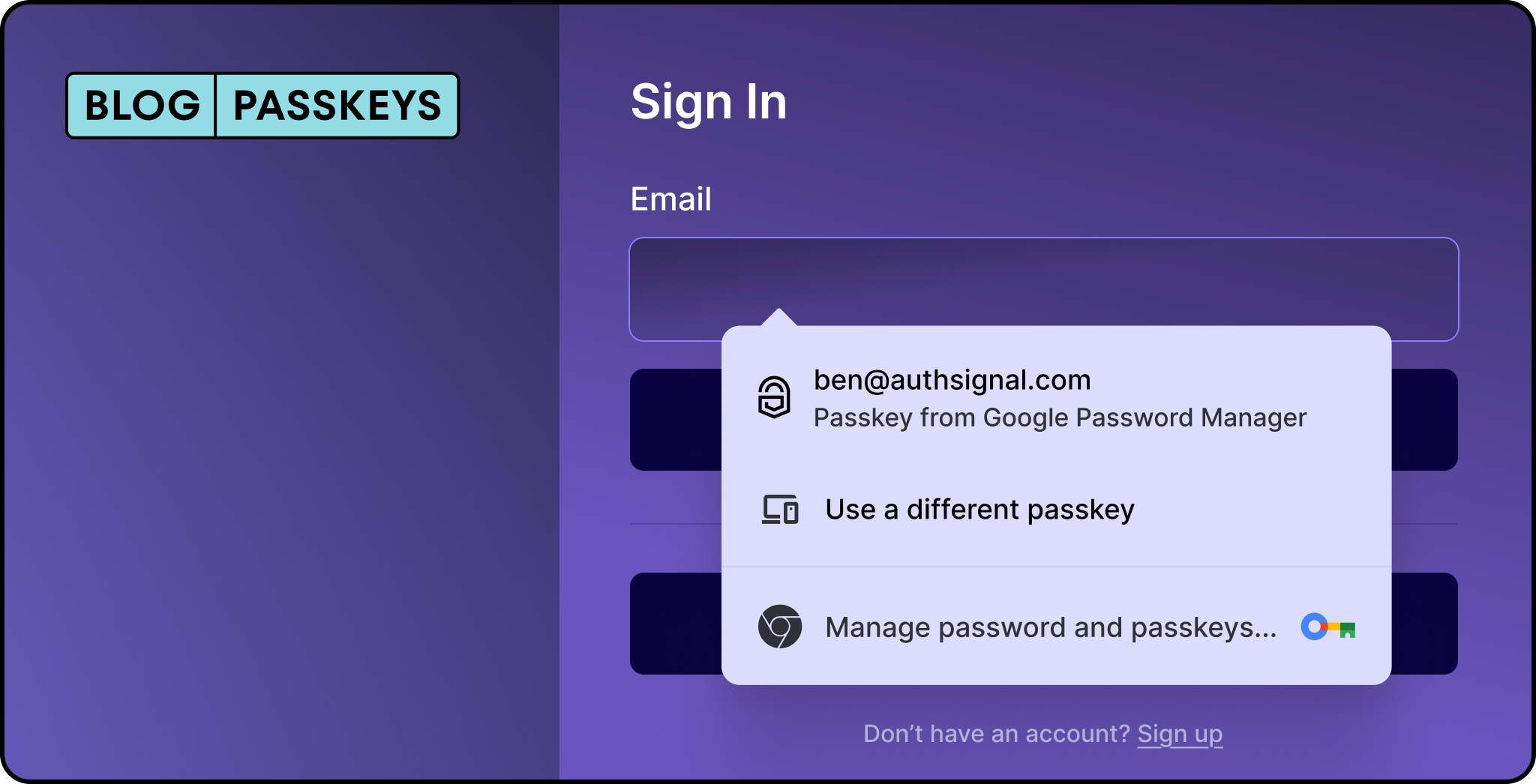
Passkeys replace passwords
The purpose of passkeys is to replace passwords on websites and applications. Initially deploying passkeys can be a step to reduce the reliance on passwords, which means that the account will still have a password, but users are only prompted for them when they can’t use passkeys to authenticate.
Your employees and customers are likely to experience the use of passwords with your organization at multiple touch points:
Sign up
On-boarding or registration
Login & Re-authentication
Access their data
Login to a service
Recurring re-authentication to refresh a session
Transaction confirmation / critical actions
Confirm transactions
Confirm intent to take critical actions

These touch-points, where your employees and customers have to provide a password, can occur more or less often, depending on how you define your policies and if any external (regulatory) requirements apply to your situation.
Generally speaking, each of these touch-points follow the same structure of things that can happen when someone is asked to provide their password:

With this in mind, you should think about what passwords mean to your organization and who would benefit from replacing them.
- What’s the cost and harm resulting from account-takeover for your organization?
- What’s the cost of maintaining your password-based infrastructure?
- How does the churn of users who forgot their passwords impact your business goals?
- How much do you spend to get people back into their account when they lost their passwords?
Think about all the teams in your organization that could benefit if the costs mentioned above would significantly reduced.





.svg)